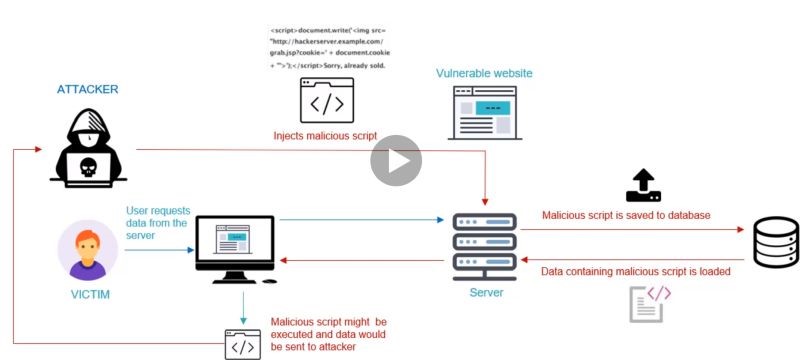
XSS injects malicious code in a vulnerable website.
XSS differ from other web attacks, in that it does not directly attack the application but rather the application user.
Problem
You create a website where you allow users to enter some html to display an ad for a car they would like to sell.
You allow your users to use html tags to make the font bold and even use different colors.
An attacker uses your website to add some malicious code in an ad containing some javascript stealing a user’s cookie information.
The unexpected user accesses the website and clicks on the attacker’s ad (which contains the malicious code).
Instantly all the current cookie information of the user is sent to the attacker.
The attacker now has access to the user current digital identity and could utilize any active cookies to get access to the user’s websites.

Solution
The Razor engine use in ASP.NET MVC Core automatically encodes all output source from variables.
It uses attribute encoding with using JavaScript to insert untrusted input.
Tag helpers will also encode input you use in tag parameters

Example of HTML encoding using Razor.
Validation can also be used to prevent XSS for example testing for a numeric value or not allowing certain special characters.
