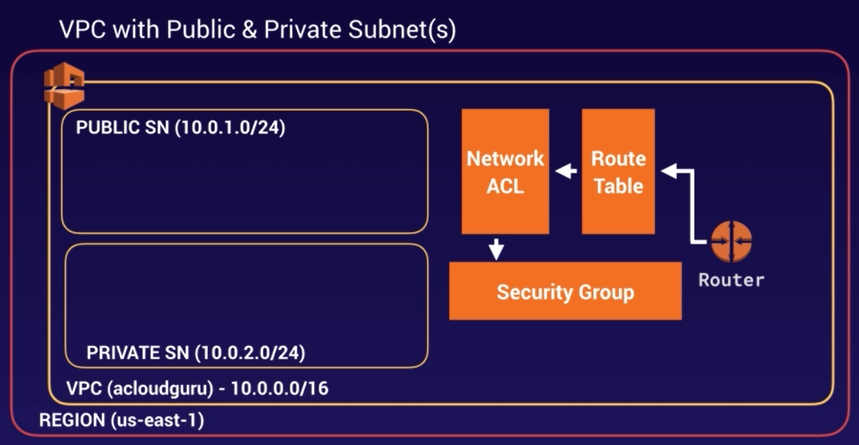
VPC - Virtual Private Cloud
What is a VPC?
VPC include multiple layers of security, including security groups and network access control lists.
Additionally, you can creeate a Hardware Virtual Private Network (VPN) connection between your corporate datacenter and your VPC and leverage the AWS cloud as an extension of your corporate datacenter.
There are a number of ways to set up a VPN.
AWS have a standard solution that makes use of a VPC with; a Private Subnet, Hardware VPN Access, a Virtaul Private Gateway, and an on-premise Customer Gateway.
A customer gateway device is a physical or software appliance on your side of a Site-to-Site VPN connection. You or your network administrator must configure the device to work with the Site-to-Site VPN connection.
When connecting a VPN between AWS and a third party site, the Customer Gateway is created within AWS, but it contains information about the third party site e.g. the external IP address and type of routing.
The Virtual Private Gateway has the information regarding the AWS side of the VPN and connects a specified VPC to the VPN.
For any new virtual gateways, configurable Private Autonomous System Number (ASN) allows customers to set the ASN on the Amazon side of the BGP session for VPNs and AWS Direct Connect private VIFs
1 Subnet = 1 Availability Zone
You cannot have a Subnet streched over multiple AZ's, but you can have multiple subnets in the same AZ
Create VPC
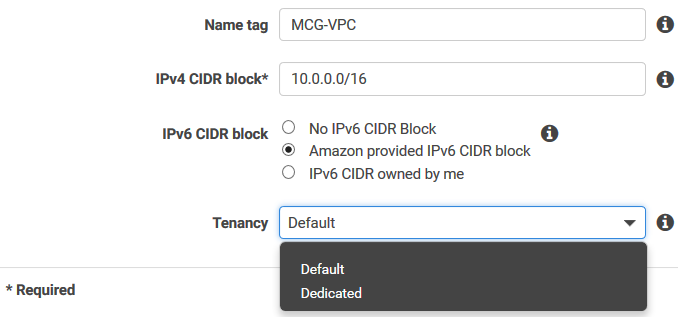
| IPv4 CIDR block |
Choose your CIDR block 10.0.0.0/16 is the biggest range supported by AWS |
| Tenancy |
Default : Multi-Tenant (shared underlying hardware) Dedicated : Instances that run on dedicated hardware (very expensive) Once a VPC is set to Dedicated hosting, it can be changed back to default hosting via the CLI, SDK or API. Note that this will not change hosting settings for existing instances, only future ones. Existing instances can be changed via CLI, SDK or API but need to be in a stopped state to do so. You can use the AWS CLI to modify the Instance Placement attribute of each instance and the VPC tenancy attribute of the VPC. |
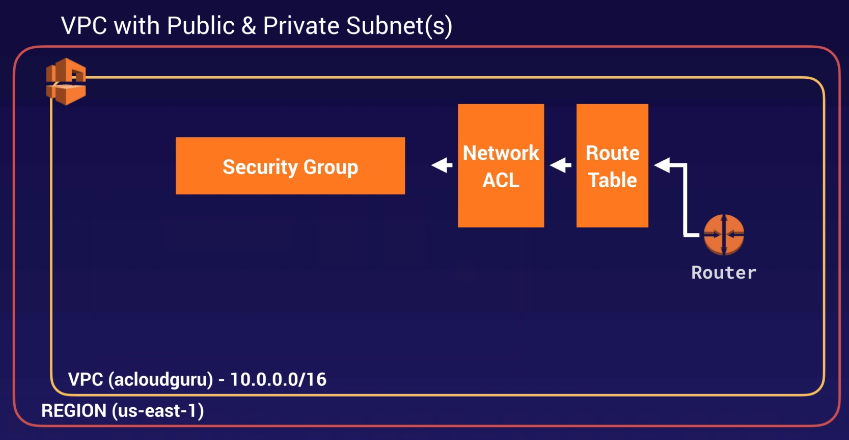
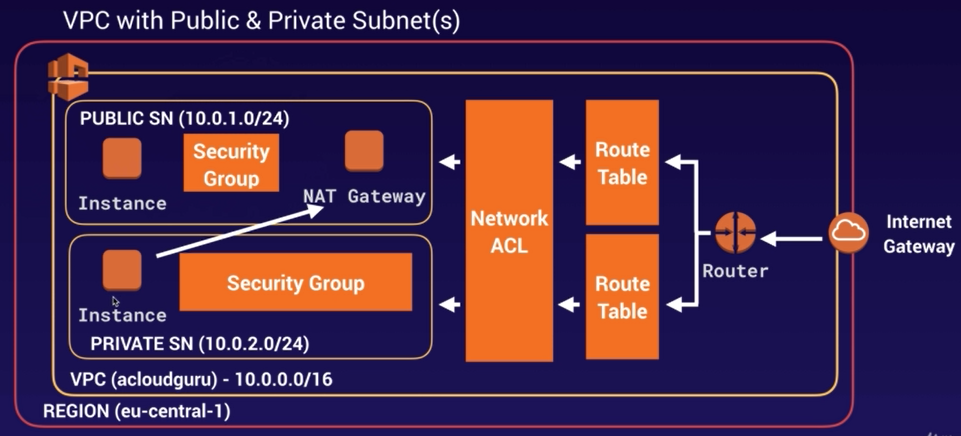
What gets created by default
- Route Tables
- Network ACL
- Security Group
Subnets
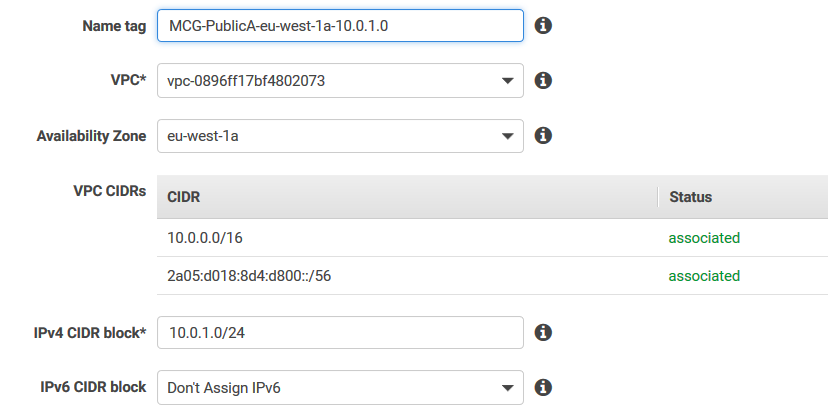
| Name tag | It is good practice to include the AZ (eu-west-1a) and the CIDR range (10.0.1.0) in your Name tag |
| VPC | Choose your VPC that this Subnet will reside in |
| Availability Zone | Choose your AZ that this Subnet will reside in |
| VPC CIDRs | Current CIDRs allocated to the selected VPC |
| IPv4 CIDR block |
Choose your CIDR range for this Subnet Internet Assigned Numbers Authority (IANA) has 3 sets of different IP addresses that is reserved for private address ranges:
AWS reserves 5 IP addresses for internal management: 10.0.0.0 : Network Address 10.0.0.1 : VPC Router 10.0.0.2 : Reserved. The IP address of the DNS server is always the base of the VPC network range plus two 10.0.0.3 : Reserved for future use 10.0.0.255 : Network broadcast address
The smallest subnet is /28, which only contains 16 IP addresses |
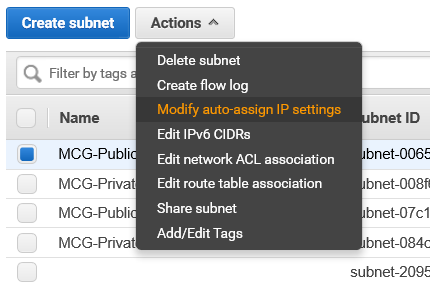
Auto-assign public IPv4 address
For your Subnets that has to be publicly accessible and may contain EC2 instances like web servers, you have to enable ‘Auto-Assign public IPv4 address’ under Actions.
Internet Gateway (IGW)
Create and attach your IGW to your VPC.
You can only attach 1 IGW per VPC.
Egress-only internet gateway basics
An instance in your public subnet can connect to the internet through the internet gateway if it has a public IPv4 address or an IPv6 address.
Similarly, resources on the internet can initiate a connection to your instance using its public IPv4 address or its IPv6 address.
IPv6 addresses are globally unique, and are therefore public by default.
If you want your instance to be able to access the internet, but you want to prevent resources on the internet from initiating communication with your instance, you can use an egress-only internet gateway.
To do this, create an egress-only internet gateway in your VPC, and then add a route to your route table that points all IPv6 traffic (::/0) or a specific range of IPv6 address to the egress-only internet gateway.
IPv6 traffic in the subnet that's associated with the route table is routed to the egress-only internet gateway.
An egress-only internet gateway is stateful: it forwards traffic from the instances in the subnet to the internet or other AWS services, and then sends the response back to the instances.
The purpose of an "Egress-Only Internet Gateway" is to allow IPv6 based traffic within a VPC to access the Internet, whilst denying any Internet based resources the possibility of initiating a connection back into the VPC.
Route Tables
Always keep your main route table as private and create an additional route table for your public Subnets.
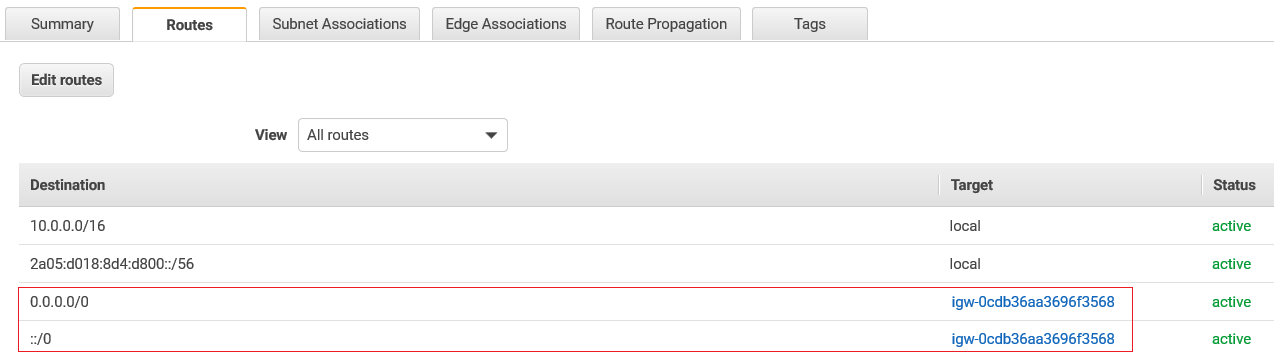
Assign all IPv4 and IPv6 addresses to your Internet Gateway.
Any Subnet associated with this route table will automatically become public for IPv4 and IPv6.
Assign your public Subnets to this route table to provide public access.
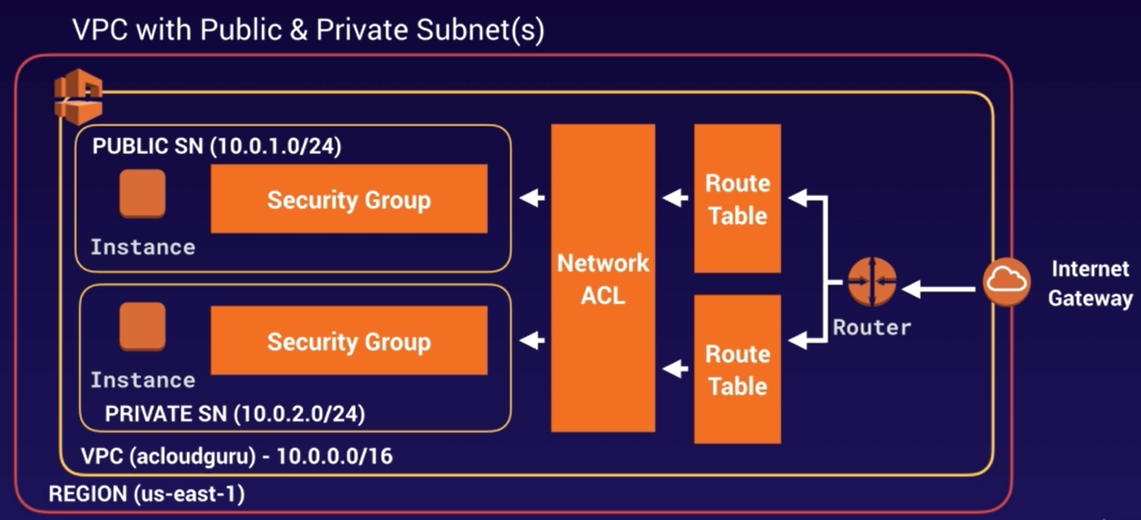
Network ACL
- Network ACL (Access Control List) are the first line of defence and are Stateless.
- They allow you to do allow rules aswell as deny rules for the same port for example.
- You can also block specific IP addresses with a Network ACL.
- If you add a DENY in your ACL, a request mighy never even reach your Security Group settings.
- Your VPC automatically comes with a default network ACL, and by default it allows all outbound an inbound traffic.
- You can create cutom network ACLs. By default ,each custom network ACL denies all inbound and outbound traffic until you add rules.
- Each subnet in your VPC must be associatd with a network ACL.If you don't explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
- You can associate a network ACL with multiple subnets; however, a subnet can be associated with only one network ACL at a time. When you associate a network ACL with a subnet, the previous association is removed.
- Network ACLs contain a numbered list of rules that is evaluated in order, starting with the lowest numbered rule
- Network ACLs have separate inbound and outbound rules, and each rule can either allow or deny traffic
- Network ACLs are stateless; responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa)
Security Groups
- Security Groups are your second line of defence and they are Statefull.
- Security Groups cannot span VPCs.
- Security Groups operate at the instance level, they support "allow" rules only, and they evaluate all rules before deciding whether to allow traffic.
Inbound Rules
Changes to your Security Group will take effect immediately!
You cannot block or blacklist a particulat port or IP address with Security Groups.
With Security Groups all inbound traffic is blocked by default and all outbound traffic is allowed.
You can attach more than 1 Security Group to an EC2 instance.
In Security Groups, you can specify allow rules, but not deny rules.
- SSH is on port 22 - Some networks will block this port. - HTTP is on port 80 - HTTPS is on port 443 - TCP is on port 0 - 65535 - MySQL/Aurora 3306 - MS SQL 1433 - The source for any IPv4 address is 0.0.0.0/0 - The source for any IPv6 address is ::/0
NAT Instances & NAT Gateways
| NAT Gateway | NAT Instance |
| Highly Available, spread over multiple AZ | Single EC2 instances (on their way out) |
Create NAT Gateway
| Subnet | Choose your public subnet |
| Elastic IP Allocation ID | Create a New EIP, by clicking the Create button |
You have to edit your route tables to point to the new NAT Gateway
NAT Instances Summary- When creating a NAT instance, Disable 'Source/Destination Check' on the instance.
- NAT instances must be in a public subnet.
- There must be a route out of the private subnet to the NAT instance, in order for this to work.
- The amount of traffic that NAT instances can support depends on the instanze size.
- You can create high availability using Autoscaling Groups, multiple subnets in different AZs and a script for automate failover.
- NAT Instances are behind a Security Group.
- Redundant inside the AZ.
- NAT Gateway can't span AZs.
- Preferred by the enterprise
- Starts at 5 Gbps and scales currently to 45 Gbps
- No need to patch.
- Automatically assigned a public IP address.
- Remember to update your route tables.
- No need to disable Source/Destination Checks.
- If you have resources in multiple AZs and they share one NAT Gateway, in the event that the NAT Gateway's AZ is down, resources in the other AZs will lose internet access. To create an AZ independent architecture, create a NAT Gateway in each AZ and configure your routing to ensure that resources use the NAT Gateway in the same AZ.
Bastion Hosts/Jump Boxes
A Bastion host is a instance in a public sub-domain used to SSH to an instance in a private sub-domain to grant internet access to the instance in the private sub-domain.
A bastion host is a special purpose computer on a network specifically designed and configured to withstand attacks.
The computer generally hosts a single application, for example a proxy server, and all other services are removed or limited to reduce threat to the computer.
It is hardened in this manner primarily due to its location and purpose, which is either on the outside of a firewall or in a demilitarized zone (DMZ public subnet) and usually involves access from untrusted networks or computers.
VPC Peering
Allows you to connect one VPC with another via a direct network route using private IP addresses.
Instances behave as if they were on the same private network.
You can peer VPC's with other AWS accounts as well as with other VPCs in same account.
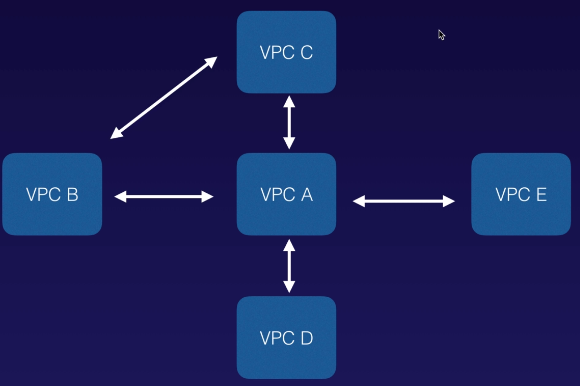
Peering is in a star configuration: ie 1 central VPC peers with 4 others. NO TRANSITIVE PEERING!!!
You can peer between regions, but VPC peering does not support edge to edge routing.
Transitive Peering
VPC B is peered with VPC A
VPC A is peered with VPC C
For you to peer VPC B to VPC C, you can't go through VPC A
You have to create a new peering connection between VPC B and VPC C
VPC Flow Logs
VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC.
Flow log data is stored using Amazon CloudWatch Logs.
Flow logs can be created at 3 levels:
- VPC
- Subnet
- Network Interface Level
Select a VPC, select actions and then 'Create flow log'
| Resources | VPC ID of your applicable vpc |
| Filter | You can choose to log Accepted, Rejected or All traffic |
| Destination | Flow log data can be published to CloudWatch logs or a S3 Bucket |
| Destination log group | You have to create a Log Group in CloudWatch to select here |
| IAM role |
- You cannot enable flow logs for VPCs that are peered with your VPC unless the peer VPC is in your account.
- You cannot tag a flow log.
- After you've created a flow log, you cannot change its configuration; for example can't associate different IAM role.
-
The following Traffic is not monitored:
1. Traffic generated by instances when they contact the Amazon DNS. If you use your own DNS server then all traffic to that DNS server is logged.
2. Traffic generated by a Windows instance for Amazon Windows license activation.
3. Traffic to and from 169.254.169.254 for instance metadata.
4. DHCP traffic.
5. Traffic to the reserved IP address for the default VPC router.
Direct Connect

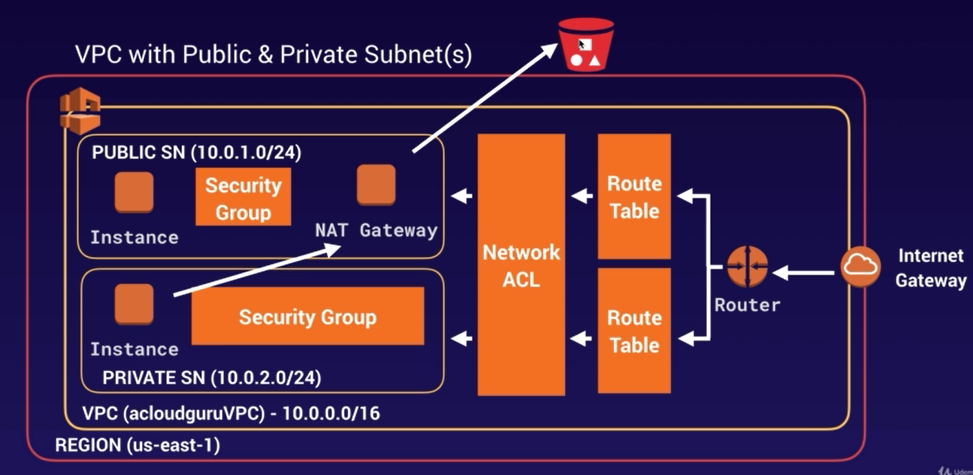
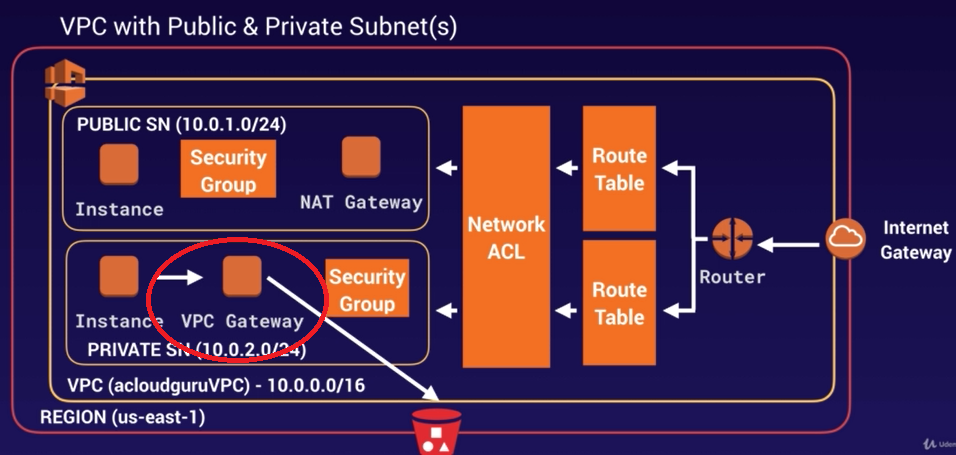
VPC Endpoints

There are two types of VPC endpoints:
- Interface Endpoints
- Gateway Endpoints
Interface Endpoints

Gateway Endpoints
Currently Endpoints support:- Amazon S3
- DynamoDB
Key Exam Tips
- When you create a VPC a default Route Table, Network Access Control List (NACL) and a default Security Group is created. - It wont create subnets or internet gateways - US-East-1A in your AWS account can be a completely different AZ to US-East-1A in another AWS account. The AZ's are randomized.
