Web Identity Federation & Cognito
What is Web Identity Federation?
- Web Identity Federation lets you give your users access to AWS resources after they have successfully authenticate with a web-based identity provider like Amazon, Facebook, or Google.
- Following successful authentication, the user receives an authentication code from the Web ID provider, which they can trade for temporary AWS security credentials.
What does Amazon Cognito provide?
- Amazon Cognito provides Web Identity Federation with the following features:
1. Sign up and sign in to your apps.
2. Access for guest users.
3. Acts as an Identity Broker between your application and Web ID providers, so you don't need to write any additional code.
4. Synchronizes user data for multiple devices.
5. Recommended for all mobile application AWS services.
Cognito brokers between the app and Facebook or Google to provide temporary credentials which map to an IAM role allowing access to the required resources.
No need for the application to embed or store AWS credentials locally on the device and it gives users a seamless experience across all mobile devices.
Cognito User Pools?
- User Pools are user directories used to manage sign-up and sign-in functionality for mobile and web applications.
- Users can sign-in directly to the User Pool, or using Facebook, Amazon, or Google.
- Cognito acts as an Identity Broker between the identity provider and AWS.
- Successful authentication generated a JSON Web token (JWTs).
Identity Pools (Federation)?
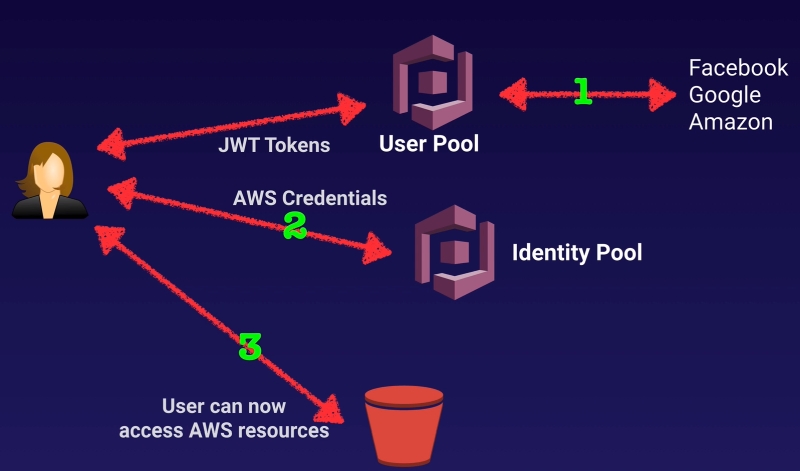
Identity Pools enable you to provide temporary AWS credentials to access AWS services like S3 or DynamoDB.
Identity Pools is all about the authorization of access to AWS resources, where User Pools is all about your actual users.
1. Users login using her Facebook credentials. Once Facebook has authenticated the user, it will pass a token to Cognito. Cognito convert this token to a JWT token and sends it to the user.
2. The user then sends the JWT token to an Identity Pool, that will grant her AWS credentials in the form of an IAM Role.
3. Using her AWS credentials and permissions granted she will be able to access AWS resources (S3 bucket (website))
- Cognito tracks the association between user identity and the various different devices they sign-in from.
- In order to provide a seamless user experience for your application, Cognito uses Push Synchronization to push updates and synchronize user data across multiple devices.
- Cognito uses SNS to send a notification to all the devices associated with a given user identity whenever data stored in the cloud changes.
- AWS supports identity federation with SAML 2.0, an open standard that many identity providers (IdPs) use.
- This feature enables federated single sign-on (SSO), so users can log into the AWS Management Console or call the AWS APIs without you having to create an IAM user for everyone in your organization.
- By using SAML, you can simplify the process of configuring federation with AWS, because you can use the IdP's service instead of writing custom identity proxy code.
- Before you can use SAML 2.0-based federation, you must configure your organization's IdP and your AWS account to trust each other.
- The general process for configuring this trust is described in the following steps:
- Inside your organization, you must have an IdP that supports SAML 2.0, like Microsoft Active Directory Federation Service (AD FS, part of Windows Server), Shibboleth, or another compatible SAML 2.0 provider.
Exam Tips
- Federation allows users to authenticate with a Web Identity Provider (Google, Facebook).
- Cognito is an Identity Broker which handles interaction between your applications and the Web ID provider.
- User Pool is user based. It handles things like user registration, authentication, and account revovery.
- Identiy Pools authorise access to your AWS resources..
